Day 41 - Terraform with AWS
Table of contents
AWS CLI installed
AWS CLI (Amazon Web Services Command Line Interface) is a command-line tool provided by Amazon Web Services to interact with various AWS services and manage your AWS resources from your local terminal or command prompt. With the AWS CLI, you can perform tasks such as creating and managing EC2 instances, S3 buckets, IAM users, and more, all through simple commands.
sudo apt install awscli
Configure AWS CLI:
As mentioned earlier, after installation, you'll need to configure the AWS CLI with your AWS access credentials (access key and secret access key), default region, and output format. You can do this by running:
aws configure

Terraform installed
To set up Terraform locally and install the necessary dependencies, follow these steps:
wget -O- https://apt.releases.hashicorp.com/gpg | sudo gpg --dearmor -o /usr/share/keyrings/hashicorp-archive-keyring.gpg
echo "deb [signed-by=/usr/share/keyrings/hashicorp-archive-keyring.gpg] https://apt.releases.hashicorp.com $(lsb_release -cs) main" | sudo tee /etc/apt/sources.list.d/hashicorp.list
sudo apt update && sudo apt install terraform
run the command to verify that Terraform is installed and accessible:
terraform version
Create AWS EC2 instance
Certainly, let's go through the steps to create and manage AWS resources using Terraform.
Step 1: Directory Structure
First, make sure your project has the following directory structure:
my-terraform-project/
├── main.tf
├── variables.tf
Provider and Resource Definitions (main.tf):
Your resource definitions for VPC, internet gateway, subnet, security group, route table, route table association, key pair, and EC2 instance can be placed in the main.tf file. Here's the revised main.tf:
terraform {
required_providers {
aws = {
source = "hashicorp/aws"
version = "5.20.0"
}
}
}
provider "aws" {
region = "ap-south-1"
}
resource "aws_vpc" "my_vpc" {
cidr_block = var.vpc-range
tags = {
Name = "my-vpc"
}
}
resource "aws_internet_gateway" "my_igw" {
vpc_id = aws_vpc.my_vpc.id
tags = {
Name = "my-gateway"
}
}
resource "aws_subnet" "my_subnet" {
vpc_id = aws_vpc.my_vpc.id
cidr_block = var.subnet-range
availability_zone = var.availability-zone
map_public_ip_on_launch = true
tags = {
Name = "puclic-subnet"
}
}
resource "aws_security_group" "my_security_group" {
name = "terraform-security-group"
description = "terraform security group to allow SSH, HTTP, and HTTPS traffic"
vpc_id = aws_vpc.my_vpc.id
ingress {
from_port = 22
to_port = 22
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
ingress {
from_port = 80
to_port = 80
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
ingress {
from_port = 443
to_port = 443
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
tags = {
Name = "trfm-sct-grp"
}
}
resource "aws_route_table" "my_route_table" {
vpc_id = aws_vpc.my_vpc.id
route {
cidr_block = "0.0.0.0/0"
gateway_id = aws_internet_gateway.my_igw.id
}
tags = {
Name = "public-route"
}
}
resource "aws_route_table_association" "subnet_association" {
subnet_id = aws_subnet.my_subnet.id
route_table_id = aws_route_table.my_route_table.id
}
resource "aws_key_pair" "my_key_pair" {
key_name = "terraform-key"
public_key = file("~/.ssh/id_rsa.pub")
}
resource "aws_instance" "my_instance" {
ami = var.ami-id
instance_type = var.instance-type
subnet_id = aws_subnet.my_subnet.id
key_name = aws_key_pair.my_key_pair.key_name
vpc_security_group_ids = [aws_security_group.my_security_group.id]
tags = {
Name = "first"
}
}
Your variables.tf file defines the input variables, which is good. You can keep this as is:
variable "ami-id" {
description = "this is a ami-variable"
default = "ami-0f5ee92e2d63afc18"
}
variable "instance-type" {
description = "this is a instance-variable"
default = "t2.micro"
}
variable "vpc-range" {
description = "this is a vpc range variable"
default = "192.168.0.0/16"
}
variable "subnet-range" {
description = "this is a subnet range variable"
default = "192.168.0.0/24"
}
variable "availability-zone" {
description = "this is a subnet avalaiblity zone variable"
default = "ap-south-1a"
}
Usage:
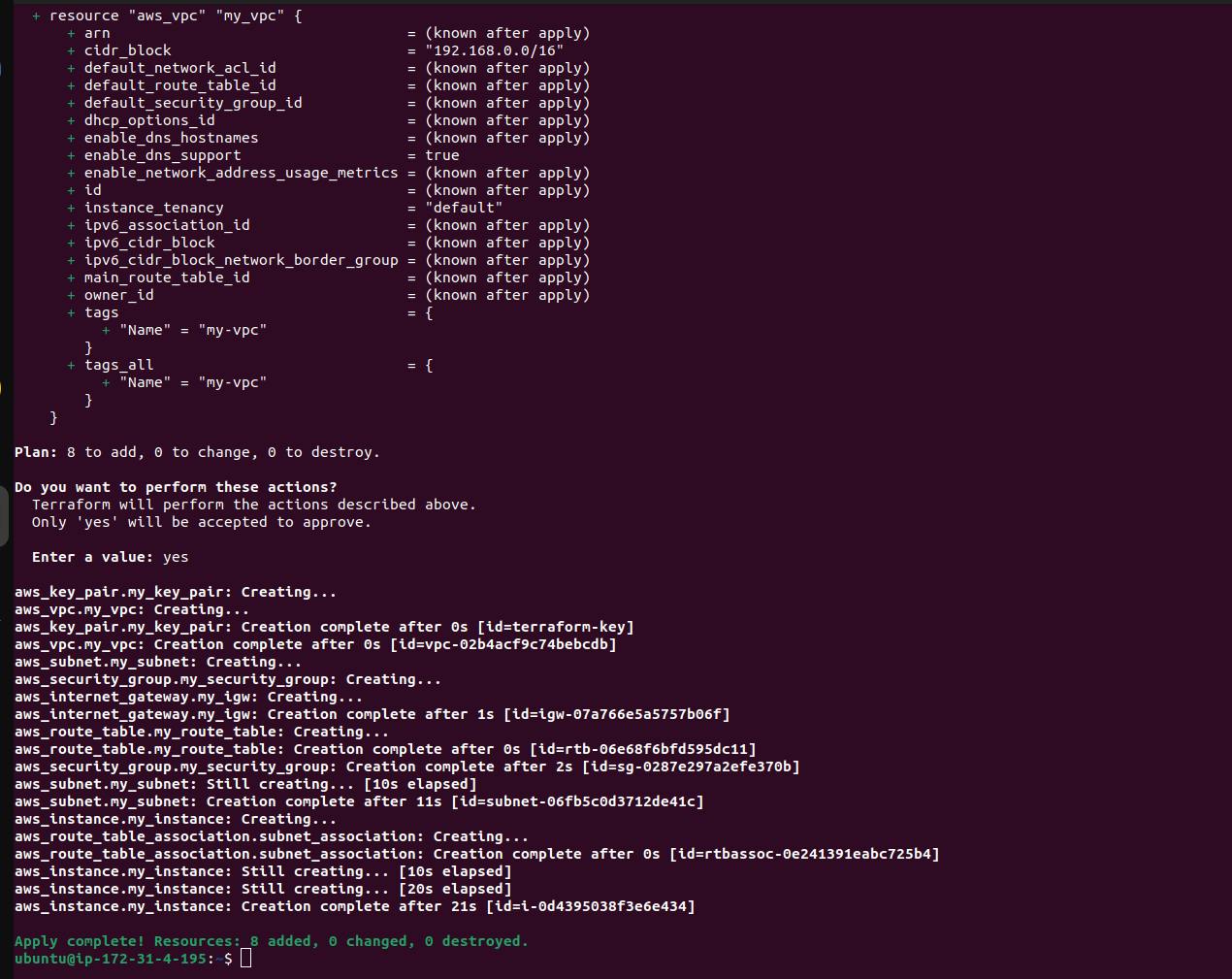
In your terminal, navigate to the directory containing these files and run:
terraform init
terraform plan
terraform apply
#if you want to destroy the infrastructure use
terraform destroy